CRTA - Exam Review
My CRTA Exam Review

My CRTA Exam Review.
I started my CRTA exam on April 4, 2025 and submitted the exam report on the same day. And received a much awaited email after 4 days stating:
Acting as an adversary you have successfully emulated Tactics, Techniques & Procedures (TTP’s) as an adversary in our Lab. Achieving this you have accomplished the end goal to ex filtrate sensitive data from the large enterprise environment. We are proudly awarding you CyberWarFare Labs Certified Red Team Analyst Badge & Certificate
Background:
Recently, I was browsing the internet to explore some red team-related certifications, as I had completed the eJPT a while ago and hadn’t been actively pursuing any new certs. Although I’ve been actively working on Hack The Box Season 7 machines, I wanted to test my knowledge through a structured assessment. That’s when I came across the CRTA certification. Surprisingly, they were offering a massive 90% discount in celebration of their 5-year anniversary. Given such an opportunity, skipping this certification was a no-brainer.

About the exam:
The Certified Red Team Analyst (CRTA) certification, offered by CyberWarFare Labs, validates advanced offensive security skills through a demanding 24-hour hands-on examination. Unlike theoretical certifications, CRTA tests real-world adversarial tradecraft by challenging candidates to breach complex, fully patched enterprise environments.
This certification proves mastery in:
- Operational tradecraft aligned with MITRE ATT&CK’s Red Team tactics
- Enterprise-scale attacks, including Kerberos exploitation in hardened Active Directory
- Segmentation bypass techniques against modern Windows/Linux systems
- Covert operations like stealth pivoting and lateral movement in hybrid networks
- Emerging threat replication to expose systemic security gaps
- Designed for practitioners, CRTA distinguishes analysts who can think like advanced adversaries — not just follow checklists. Its performance-based assessment mirrors actual breach scenarios, making it a respected benchmark for red team professionals.
Key differentiators:
✔ 100% practical exam (no multiple-choice)
✔ Focus on modern, patched environments
✔ Covers both external & internal enterprise attack paths
Prep:
The Red Team Analyst Course by CyberWarFare Labs is a comprehensive, hands-on program designed to transform security professionals into skilled adversarial emulation specialists. The course begins with foundational concepts, covering Red Teaming principles, attack lifecycles, and infrastructure setup, before diving into enterprise technologies (web, network, cloud) and lab configuration.
Participants gain practical experience in external offensive operations, learning to enumerate exposed assets, exploit web/network services, and conduct post-exploitation activities. The training then shifts to internal offensive operations, teaching Active Directory exploitation, network segmentation bypass, and lateral movement — culminating in full domain compromise. A real-world case study reinforces skills through a lab mapped to the MITRE ATT&CK framework, where students practice stealth persistence (LOLBAS), data exfiltration, and evasion. The course concludes with exam preparation, ensuring readiness for the rigorous 24-hour CRTA certification assessment.
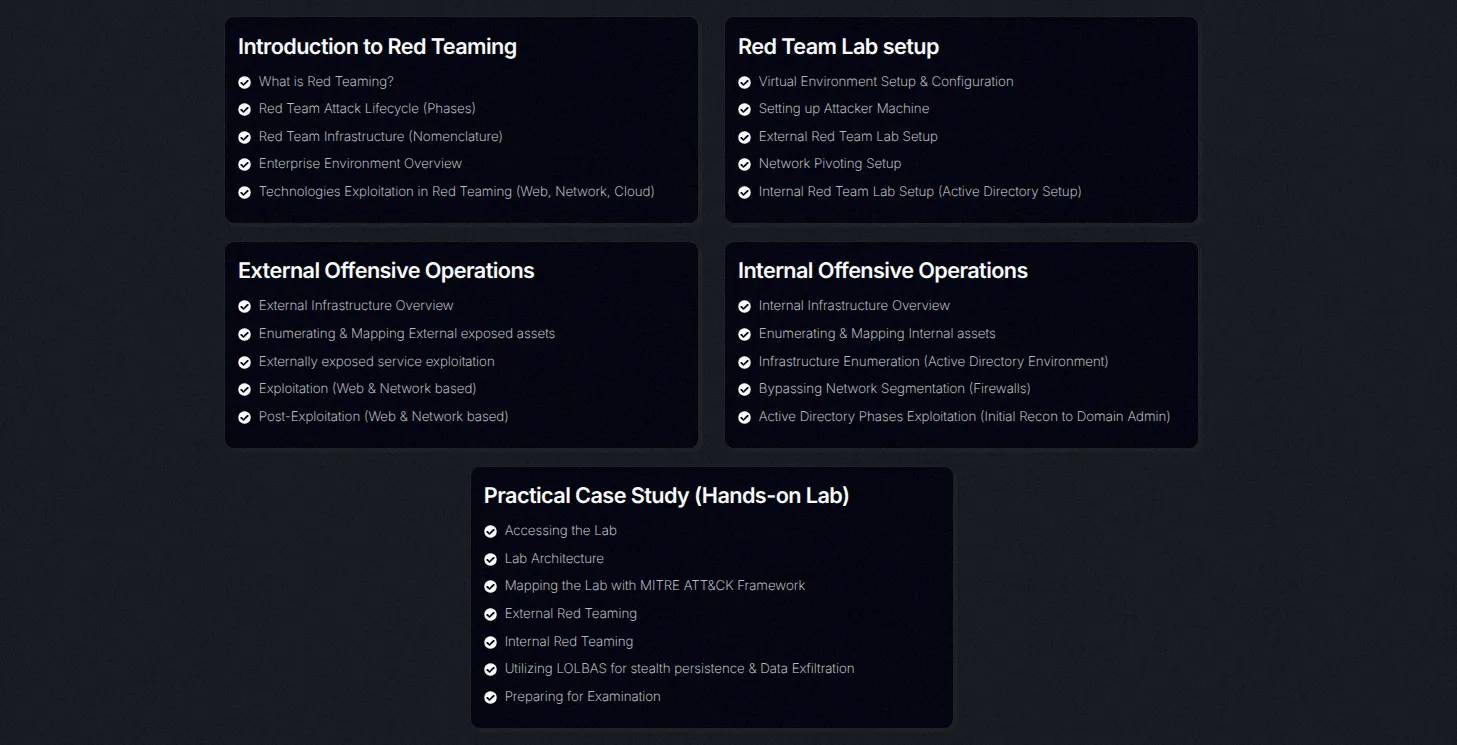
TBH as I mentioned that I was actively playing the HTB season 7 machines so I decided to skip the course and lab and directly scheduled my exam.
Exam:
I initially planned to take the CRTA exam on April 4th, a weekend at the end of my holiday week, thinking I’d have ample time to complete it. However, when I went to schedule, there were no available slots for the entire next month. Thankfully, after reaching out to support, they kindly offered me a Saturday slot — but at 1:00 AM. This meant sacrificing sleep, which, in hindsight, was my first mistake.
Just two hours before the exam, I finished solving the Akerva HTB Fortress, which took me 4.5 to 5 consecutive hours. By the time the exam started, I was exhausted — definitely not ideal. Still, I powered through with a strong coffee and began.
- Initial Phase (0–30 mins): Smooth sailing — I gained initial access to the public machine quickly.
- Post-Exploitation (Next 15 mins): Rooted it without much trouble.
- AD Portion (The Real Challenge): Here’s where things got messy. My tools weren’t cooperating, fatigue set in, and progress stalled. After 1.5 hours of frustration, I made a critical decision — a 30-minute power nap.
That short break completely reset my focus. When I resumed, things started falling into place, and I finished the remaining objectives in about 2 hours.
- Don’t Underestimate Preparation — The exam was tougher than I expected. Study the lab material thoroughly — it’s essential.
- Rest is Non-Negotiable — Never go into an exam sleep-deprived. A fresh mind makes all the difference.
- Document EVERYTHING — Screenshot every step (yes, EVERYTHING). For my report, I used Obsidian, but tools like Notion work too.
If you’re preparing for the CRTA, take it seriously, rest well, and trust the process. It’s a demanding but rewarding challenge!
I hope this blog is enough to provide you the guideline you needed. At the end here is my shiny certificate xD.
Stay in the loop with my latest content – follow me on Medium for more!