Royal Elementor Addons Vulnerability
A Deep Dive into the Royal Elementor Addons Plugin Vulnerability and How to Protect Your WordPress Site.

CVE: CVE-2024–3889
Date: 23 Apr 2024
Severity: Medium
Attack Vector: Network
Overview
WordPress is a popular platform for building websites, with countless plugins and themes designed to add functionality and customization. However, with its popularity comes a range of security risks. One such risk is a vulnerability discovered in the Royal Elementor Addons and Templates plugin, which affects all versions including 1.3.971. This vulnerability allows for Stored Cross-Site Scripting (XSS), a potentially severe security threat.
What is Stored Cross-Site Scripting (XSS)?
Cross-site scripting, or XSS, is a type of security vulnerability commonly found in web applications. It occurs when an attacker can inject malicious scripts into a website, which then run on a visitor’s browser. There are two main types of XSS:
- Stored XSS: The injected script is stored in the database or another location, meaning it will continue to run each time the affected page is accessed.
- Reflected XSS: The script is not stored, but instead is sent to the user in response to an action, like clicking a link or submitting a form.
What is the Royal Elementor Addons Plugin?
The Royal Elementor Addons and Templates plugin is an extension for the Elementor page builder in WordPress. It provides additional widgets and templates to enhance the design and functionality of WordPress websites. One of these widgets is the “Advanced Accordion,” which allows users to create foldable sections on a webpage.
The Vulnerability in the Advanced Accordion Widget
The vulnerability arises from insufficient input sanitization and output escaping. In simpler terms, this means that the plugin does not properly clean or “sanitize” the data entered by users, allowing malicious scripts to be injected or you can say that there is no proper input validation. The output escaping process, which should ensure that data displayed on a page is safe, is also inadequate.
Specifically, the vulnerability is related to the accordion_title_tag attribute. An attacker with contributor-level access or higher can exploit this weakness to inject web scripts into pages that contain the Advanced Accordion widget. When someone accesses the page with the injected script, the script is executed in their browser, leading to harmful outcomes like data theft, session hijacking, or malware distribution.
How to Protect Your WordPress Site
If you use the Royal Elementor Addons plugin, it’s crucial to take immediate steps to secure your website:
- Update the Plugin: Check for the latest version of the Royal Elementor Addons plugin and update it immediately. Updates often contain patches that fix known vulnerabilities.
- Use a Security Plugin: Consider installing a security plugin that can scan for vulnerabilities and protect against common attacks like XSS.
- Limit User Access: Ensure that only trusted users have contributor-level access or higher. Regularly review user roles and permissions.
- Regular Backups: Maintain regular backups of your WordPress site. In case of a security breach, you can restore a clean version of your site.
- Implement a Web Application Firewall (WAF): A WAF can help filter out malicious traffic and protect against common web vulnerabilities.
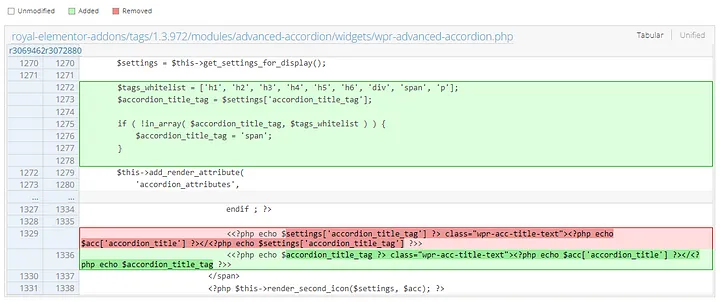
The code snippet demonstrates the introduction of a whitelist to validate user input, preventing potentially harmful HTML tags from being injected into the output. By ensuring that only predefined safe tags are used, the risk of Stored XSS is significantly reduced. This is an important security measure to protect WordPress sites from malicious attacks.
The vulnerability in the Royal Elementor Addons and Templates plugin highlights the importance of staying vigilant about website security. By understanding the risks and taking proactive measures, you can help protect your WordPress site from security threats like Stored Cross-Site Scripting. Keep your plugins and themes updated, use security tools, and be cautious with user permissions to reduce the risk of exploitation.
Resources
Thanks for reading — I hope this blog has helped you learn something new and useful.
Stay in the loop with my latest content – follow me on Medium for more!