AirTech CTF 2024 - Back To The Bases
A network forensics CTF chall. writeup.

Let's get Cracking...
Challenge 01: Back to the bases
There was a Wire Shark file given in order for us solve the challenge. You can also download the challenge file by clicking here
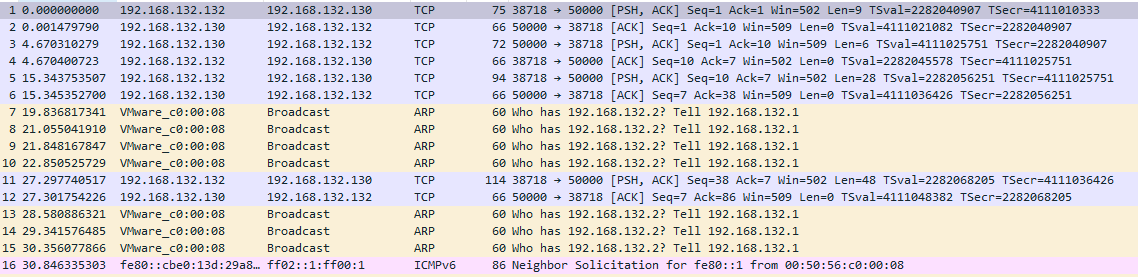
When I opened the file I noticed that there are some TCP packets.
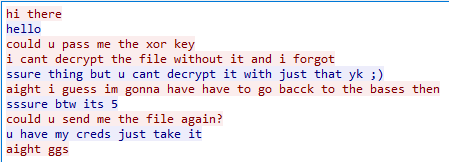
So without any delay I followed the TCP Stream from Analyze > Follow > TCP Stream menu. After following it I found the following chat.
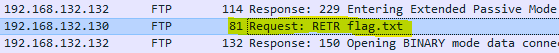
As they are talking about a file. So I applied the FTP filter and found a flag.txt file.
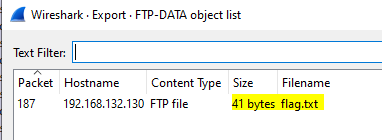
So I extracted it from File > Extract Object > FTP Data.
After saving and opening the file I found the following text.
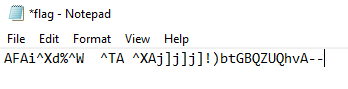
AFAi^Xd%^W ^TA ^XAj]j]j]!)btGBQZUQhvA--
Now if you remember from the chat there where two more leads as well.
- Can you pass me the
XORkey. - ssure btw its
5
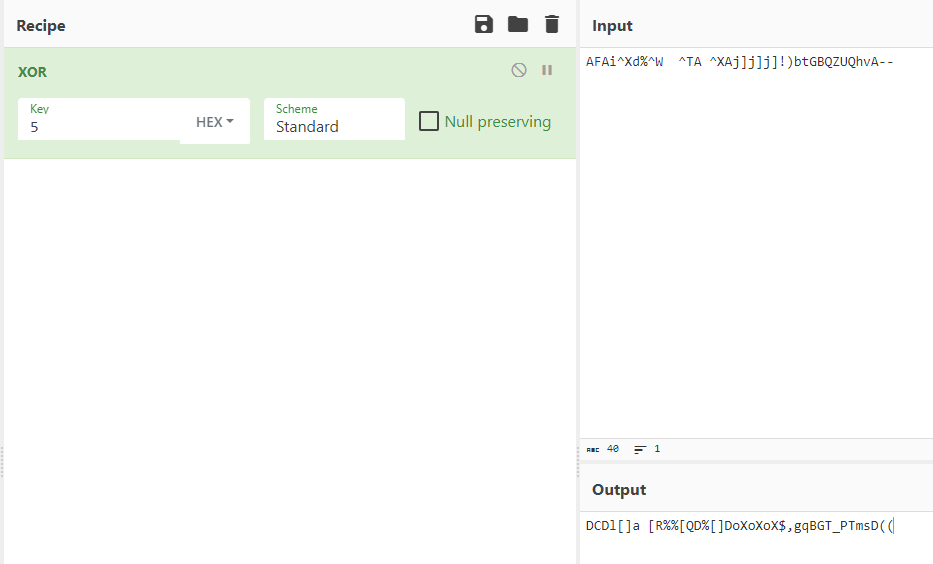
So I simply opened CyberChief and typed XOR and used 05 as the key but sadly it didn't work.
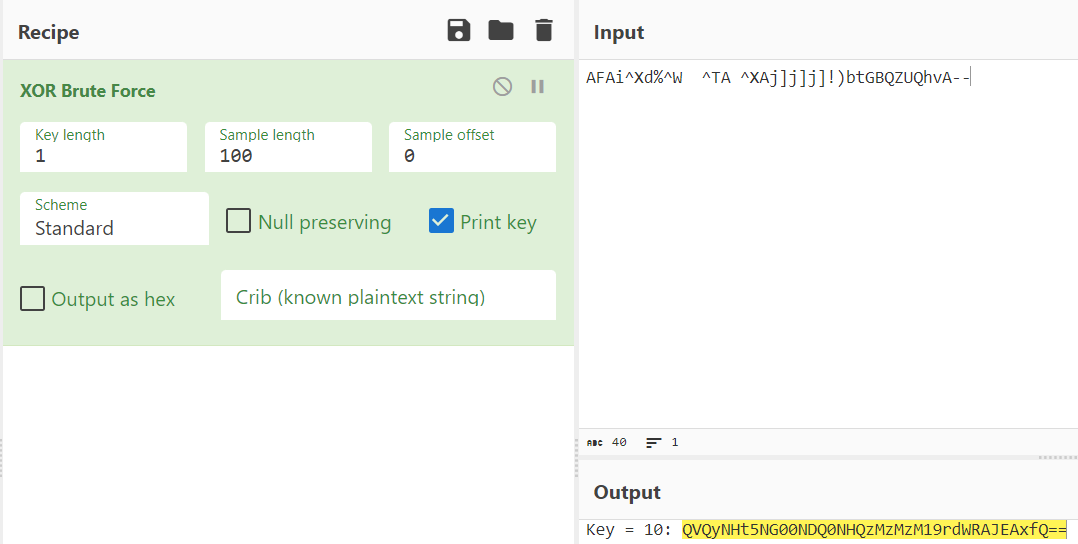
But when you have a key you always have the option to Brute Force it. When I Brute Forced the cipher I found a base64 encoded string.
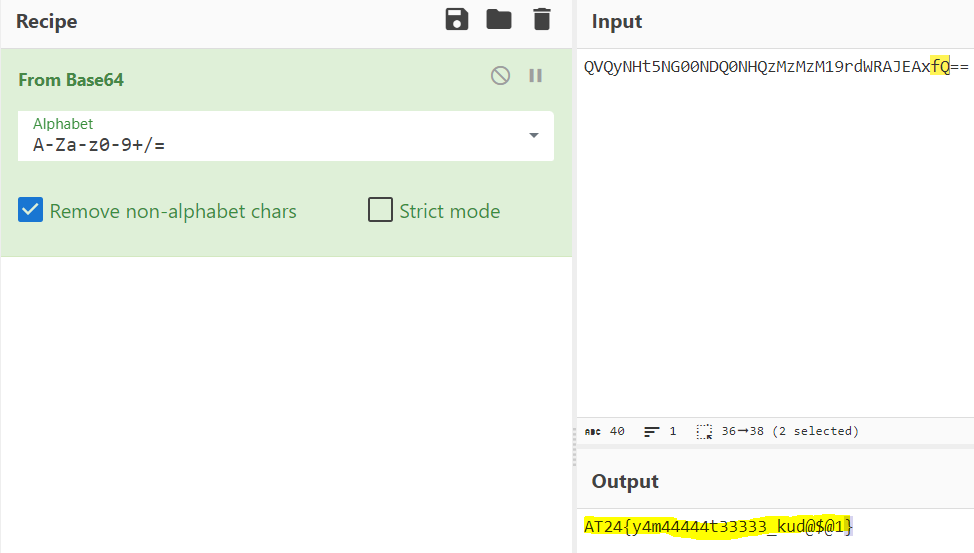
Simply decoded the string and got the flag.
Flag: AT24{y4m44444t33333_kud@$@1}
Stay in the loop with my latest content – follow me on Medium for more!